Cost Effective Managed IT Services Tampa for Small and Big Services
Cost Effective Managed IT Services Tampa for Small and Big Services
Blog Article
Increase Efficiency and Protection Through Managed IT Assistance Solutions
Managed IT sustain solutions have actually arised as an important part in guaranteeing that organizations can efficiently browse the intricacies of a digital setting. The harmony in between increasing performance and boosting safety and security through these solutions offers a calculated benefit that boosts functional effectiveness and safeguards sensitive data.
Benefits of Managed IT Support
By offering aggressive tracking and maintenance, handled IT sustain services boost functional effectiveness and boost cybersecurity procedures for services. These services aid in determining and addressing possible issues prior to they escalate, consequently minimizing downtime and guaranteeing seamless operations. With regular monitoring of networks, web servers, and gadgets, handled IT sustain teams can find abnormalities promptly and take rehabilitative activities promptly. This aggressive technique not only prevents pricey disturbances but likewise enhances general system performance.
Furthermore, handled IT sustain services provide services accessibility to a team of experienced professionals with varied experience - managed services Tampa. This implies that companies can benefit from specialized expertise and experience without the need for in-house hiring and training. By outsourcing IT support, companies can concentrate on their core tasks while leaving their technological infrastructure to capable hands
Along with operational performance, managed IT support services play a crucial duty in improving cybersecurity defenses. With the continuously developing hazard landscape, having actually committed professionals monitoring and safeguarding systems is crucial. Managed service carriers can apply robust safety and security steps, such as firewalls, file encryption, and anti-virus software program, to guard sensitive data and avoid cyber attacks. In general, the proactive tracking and comprehensive support supplied by handled IT solutions are very useful for services aiming to optimize performance and shield their digital assets.
Boosted Performance Solutions
Implementing innovative productivity remedies can improve workflows and enhance efficiency within an organization. Information analytics can aid recognize fads, patterns, and locations for enhancement, allowing companies to make data-driven choices that drive performance.
Enhanced efficiency options also assist in better collaboration among team members. This cultivates synergy, imagination, and innovation, ultimately leading to enhanced productivity end results.
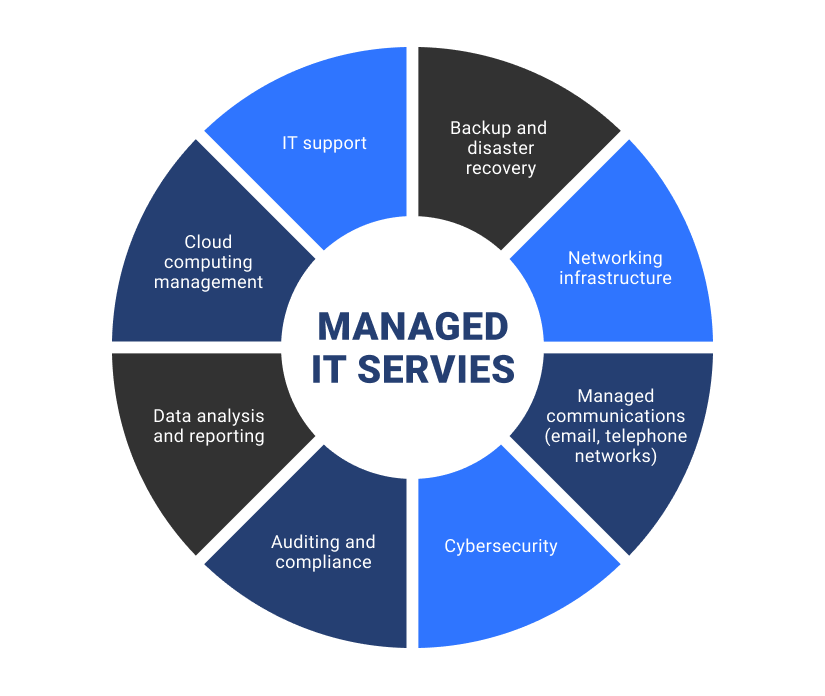
Strengthening Data Protection Measures
Exactly how can organizations boost their information protection gauges to secure sensitive information and reduce cybersecurity dangers successfully? Enhancing information security actions is critical in today's digital landscape to secure useful information from harmful hazards. One critical step is implementing robust file encryption protocols to secure data both at remainder and in transportation. By securing sensitive information, organizations can make sure that even if data is compromised, it stays illegible to these details unauthorized parties.
Moreover, carrying out multi-factor authentication (MFA) adds an added layer of security by requiring individuals to provide numerous types of verification before accessing sensitive data. This dramatically reduces the threat of unapproved gain access to, even if login credentials are endangered - managed services Tampa. Routine security audits and vulnerability assessments are also necessary to determine and deal with prospective weak points in the company's security infrastructure proactively
In addition, establishing rigorous accessibility controls and customer approvals assists restrict the direct exposure of delicate information to just certified personnel. By defining who can access what details and implementing a the very least opportunity design, companies can reduce the threat of data breaches and insider hazards. Overall, a thorough technique to information safety and security, consisting of encryption, MFA, routine audits, and access controls, is crucial in protecting delicate info and boosting cybersecurity defenses.
Aggressive IT Surveillance and Upkeep
To strengthen their total cybersecurity position and make sure constant functional effectiveness, organizations should prioritize proactive IT monitoring and maintenance as a crucial element of their handled IT sustain solutions. By continually monitoring IT framework, companies can find abnormalities, vulnerabilities, or indicators of putting in jeopardy failings quickly, making it possible for quick remediation actions to be taken.
By proactively keeping IT systems, companies can minimize the risk of vulnerabilities that can be made use of by cybercriminals. This preventative maintenance strategy not just increases general system performance but additionally makes sure that the you can find out more organization's IT setting stays durable versus developing cyber dangers.
Affordable IT Assistance Solutions
Reliable administration of resources is vital for organizations seeking to maintain an equilibrium between high quality IT support solutions and cost effectiveness. Additionally, by outsourcing IT support to a taken care of service copyright, organizations can profit from the experience of a team of specialists at a fraction of the expense of working with an internal IT division.
Handled IT services additionally help in minimizing downtime through proactive surveillance and speedy look at more info issue resolution, eventually saving businesses money that would have been lost throughout durations of inactivity. These solutions can scale up or down based on the organization's requirements, ensuring that companies pay only for the services they need. By leveraging cost-efficient IT support solutions such as handled services, organizations can maximize their IT procedures while maintaining costs in control.
Final Thought

Report this page